How to create a website using WordPress/How to use plugins/No-code construction blog
[Thinking about WordPress security] Actual case of tampering ①
At HanamiWEB Online School,
●Ask questions in real-time in the virtual study room!
●Ask as many questions as you want via chat!
●E-learning materials that you can learn as much as you want, 24 hours a day!
All included for just 2,500 yen/month!
wordperss is an easy target!
Have you ever heard of a story like this? Here is an actual case of WordPress tampering.
Learn about these cases and take appropriate security measures!
The following article provides detailed information on how to protect your WordPress site from security threats.
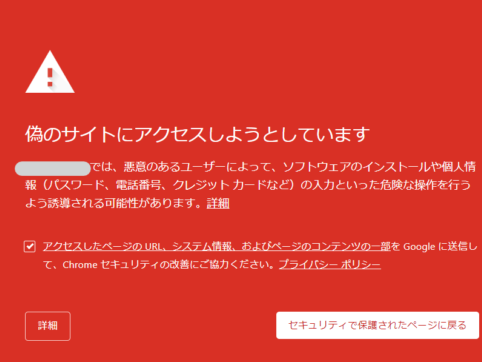
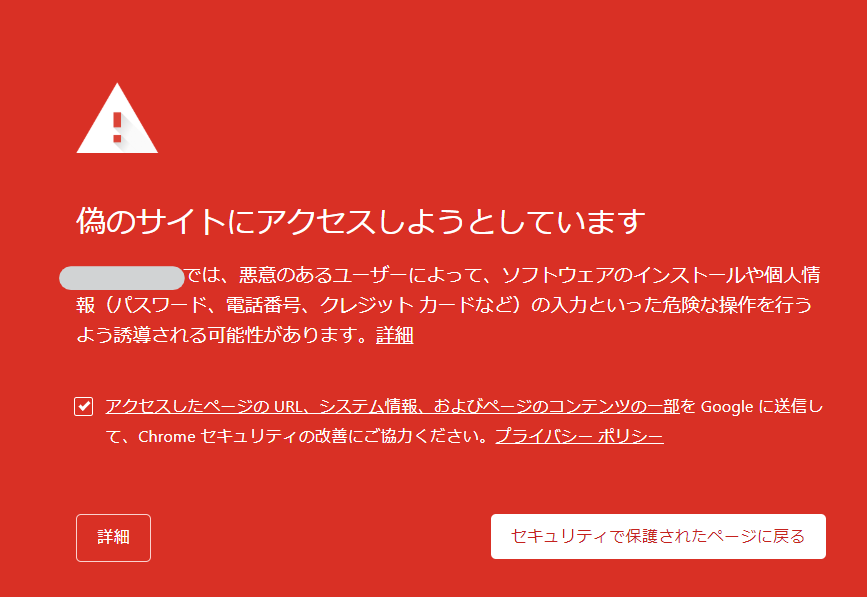
The site suddenly turned red and said "You are about to access a fake site."
Suddenly, the site turned red and displayed the message "You are about to access a fake site," and the actual site could no longer be displayed.
Additionally, clicking back on a secure page redirects you to another site.
At this stage, I finally realized that I was being attacked by hackers.
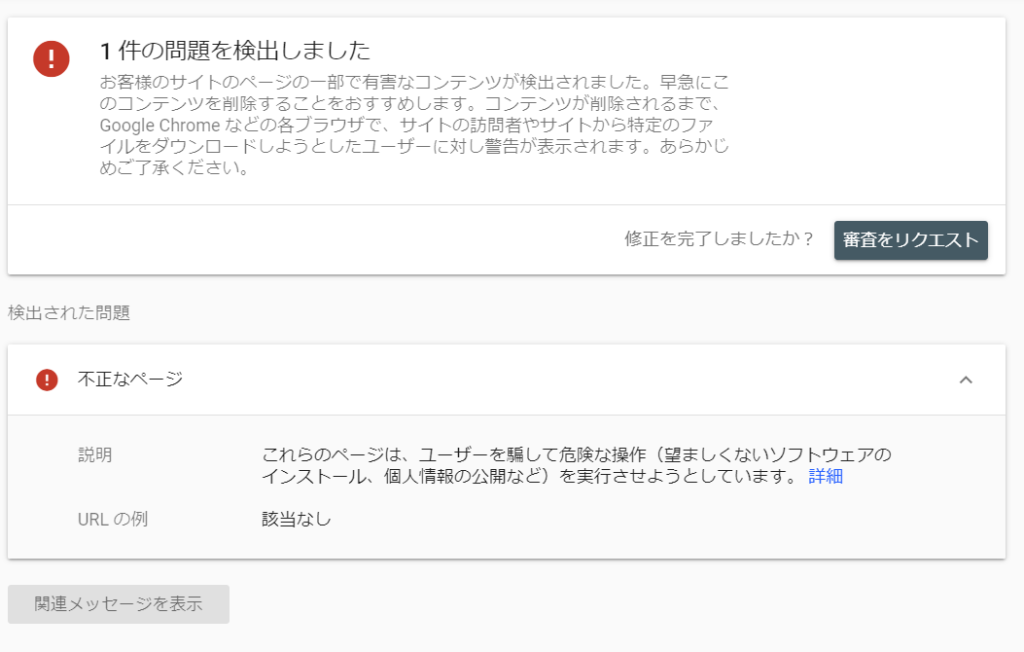
The Search Console also warns that "1 problem was detected."
I received a notification from the Seaech console. When I accessed it,
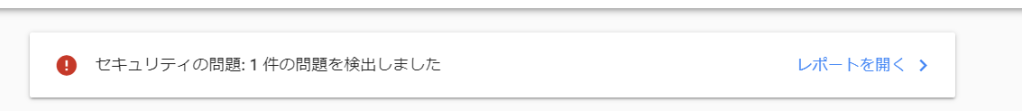
When you open the report
WordPress was attacked by a hacker
I couldn't access it from the website, so I accessed the file via FTP. (You can also use the file manager provided by the server.)
A large number of files and folders other than the standard files provided by WordPress had been accumulated.
Delete all the files that have been created
I removed all files that are not related to wordpress.
It keeps increasing even if you delete it
Even after deleting it, the number of copies increased when I reconnected via FTP. At this point, I predicted that an automatic propagation program was embedded in the php file.
The index.php file was tampered with
When I accessed the site again, the index.php file had not been deleted from the list of files that had been added, so I thought this was suspicious and opened the file, where I found that a large amount of malicious code had been added.
I removed all the unnecessary code in index.php.
The .htaccess file was also tampered with.
When I clicked on the button to go to a protected site, I was redirected to a site I didn't recognize, so I assumed that the redirect had been set up in the .htaccess file. When I checked the .htaccess file, I found that the redirect had been added.
I have also removed this code.
Delete all the attacked files and codes
Even after correcting all the files and codes I could think of, the message "You are about to access a fake site" still appears on the top page.

This is displayed by Google, so I applied for it in the Search Console.
[Request a review] Click this button and wait for your application to be reviewed.

WordPress on the same server was also affected.
There is no red "You are about to access a fake site" message on the top page

The following notification has not been received in the search console

However, when I checked the contents of the files with FTP, I found that files I did not recognize had proliferated. I thought, "I should change my password!" and tried to access the management screen, but the login screen did not appear because I did not have the necessary access permissions. The files had been tampered with so that they could not be accessed.
Delete all files added during the attack
As before, I deleted all the files I didn't recognize, but I still couldn't access the admin page, and checking the file permissions didn't fix it.
The .htaccess file was tampered with.
The following code was added to the .htaccess file. After deleting this code, I was able to successfully access the login screen.
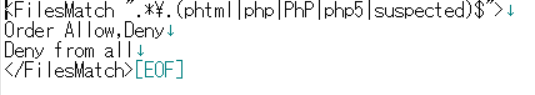
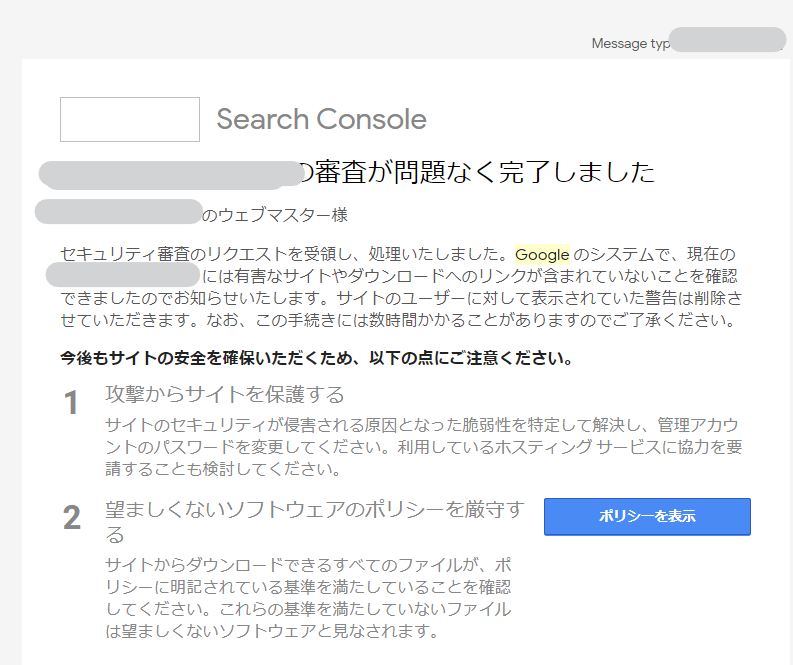
Three days later, the search console notified me that the review had been completed without any problems.
The review went through successfully and the red warning was removed from the site.
The top page is not displayed
Since the malicious files were simply deleted from the FTP server, it was difficult to grasp that the files had been tampered with, and in addition to visibly deleting the malicious files, files were also being rewritten.
Since it was a 500 error, the .htaccess file is the suspect.
I looked at the contents but couldn't find any strange statements, so I re-uploaded the .htaccess file which was working fine on other sites and the problem was solved!
However, there is still more unseen tampering...
Redirect settings are embedded in the admin panel
The admin bar is displayed, so I thought, "Isn't it strange that I'm still logged in after a while?" and tried to switch to the dashboard.
I was redirected to an unfamiliar login screen. I didn't enter any information here.
Redirect = .htaccess
I suspected that this was the case, but since I had just replaced the .htaccess file, I suspected that it was functioning somewhere other than .htaccess.
- Delete the wp-admin file that is behaving strangely
- Download the wordpress file from the official wordpress website
- Upload wp-admin file
Now it's back to normal!
The code was embedded in an invisible place, and when you tried to enter the admin screen, you were redirected.
This solves everything.
What to do if WordPress is attacked by a hacker
It may be difficult to solve the problem by yourself. First, strengthen the security of WordPress.
Below are some of the security measures that can be implemented using plugins:
The following explains how to enhance security by adding to the .htaccess file.
This explanation will be given using xserver, but security can also be strengthened from the server's administration panel.
What hanami-web can help you with
We will solve the problem on a contingency fee basis. Since we cannot guarantee a solution, we will work on a contingency fee basis.
We also hope to be of help to you in terms of security measures and solutions by collecting many case studies and posting them on our blog.
This article is available only to those who have read it and agree to us introducing it as a case study.
From 55,000 yen
In the case we introduced here, the cost is 55,000 yen.
Feel free toPlease contact us.
Released as soon as the next morning! Weekends and holidays are also available!
Super rush website creation plan
We offer a rush website creation plan for those who need a website in a hurry!
We can publish your content as soon as the next morning, even on weekends and holidays! If you have any questions, please check the details below!
Latest Articles